“
I heard that AW changed the machine (software).
Two people earned tens of millions.
I’m jealous
I didn’t earn much money myself.
Just try to do it.
In fact, in the process of doing it, I know that it is illegal.
But I always think I will stop in time.
You wouldn’t have caught me.
"
On September 16, 2021, according to the clues, Zhoucun police came to a criminal den hidden in a local residential area and cracked down on a criminal activity of illegally registering and selling WeChat. At the moment of opening the door, the scene in front of us shocked the investigators.
In the living room of the crime den, there are four white iron shelves filled with mobile phones. These mobile phones are all turned on normally, and do not need manual operation, and they are automatically carried out according to the process of popping up the interface of registering WeChat, inputting the mobile phone number and setting the password. In the computer being used at the scene, the investigators extracted hundreds of thousands of registration data.
This criminal activity can be discovered, but also from a notice of investigation received by Zhoucun Branch.
A "technology company" hidden in a private house
On the morning of September 13th, 2021, Zhoucun Branch of Zibo Public Security Bureau of Shandong Province received an investigation report that a local young man named A Cheng (a pseudonym) was suspected of helping information network criminal activities. Through cross-examination, the police learned that this person had built a platform for group control of mobile phones for an electronic technology company registered in zhoucun district, which was used to illegally register WeChat accounts.
After investigation, the operator of this electronic technology company is Gong Xiaoyu (a pseudonym), born in 1988 in Huantai County, Zibo City, Shandong Province. This company has no normal business address, registered employees, finance, etc. The two houses rented by Gong Xiaoyu are his company’s office space.
On September 16, 2021, the police divided into two groups and captured Gong Xiaoyu, the leader of the criminal gang, and other members. After entering the criminal den, the police found that the house was full of mobile phones.

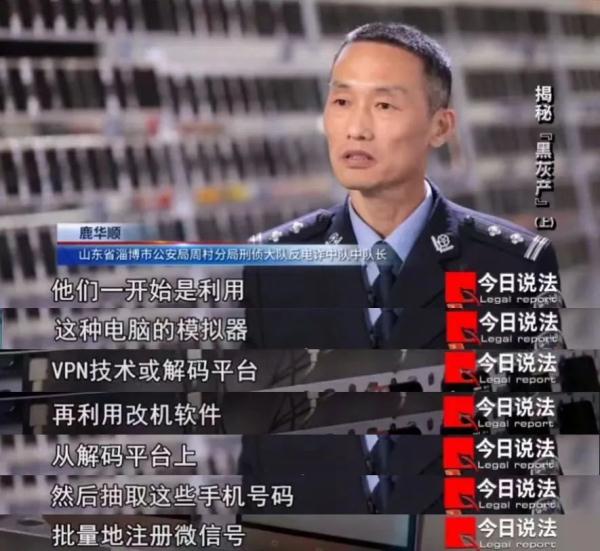
The police learned that the criminals constantly modified the basic information of the mobile phone by changing the software, and at the same time invaded the underlying program of WeChat App. By modifying the underlying code of WeChat App, they bypassed Tencent’s registration security audit system and illegally obtained the registration information of WeChat and the content of SMS verification code, so as to realize the repeated registration of WeChat account on the same mobile phone. After counting, there are more than 3,000 mobile phones used to register micro-signals in the dens.
One of the computers has logged into an overseas instant messaging software called Telegram, and the chat records show that the criminal dens and overseas criminals are talking about the quantity and transaction price of micro-signals unscrupulously.
Investigators extracted hundreds of thousands of registration data from the computer, which means that hundreds of thousands of unnamed WeChat accounts were sold abroad at the time of the incident for telecom fraud, online gambling and other activities.
It has been verified that Gong Xiaoyu’s criminal gang registered more than 3 million micro-signals in total, and settled through virtual currency, making illegal profits of more than 10 million yuan. In November 2021, fifteen suspects in Gong Xiaoyu’s criminal gang were all killed by the police.
However, the black and gray industrial chain of registering WeChat accounts in batches has already reached a certain scale in China, and Gong Xiaoyu’s criminal gang is only a link in this black and gray industrial chain. In order to completely destroy the criminal interest chain, the police decided to trace it from the source.
Constantly upgraded software for changing the machine
Investigators found that suspects must solve two key problems in order to register WeChat accounts in batches. One is to have mobile phone change software, and the other is to have a steady stream of registered WeChat mobile phone numbers.
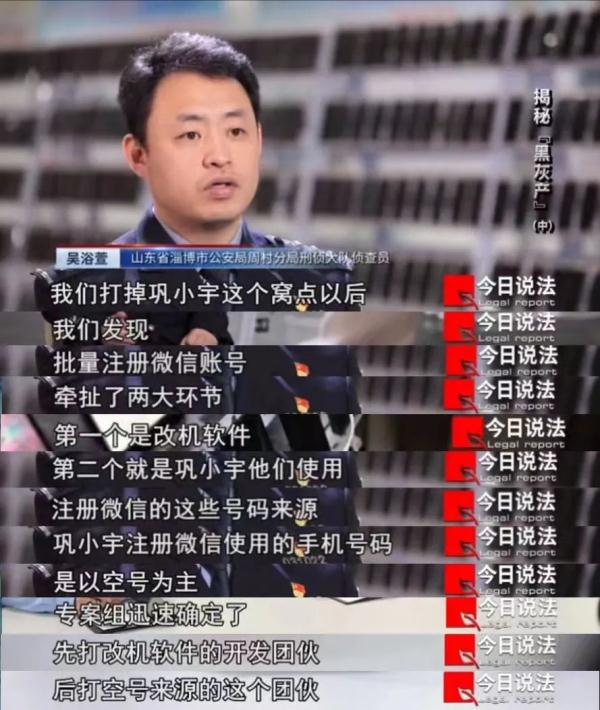
According to Gong Xiaoyu, in 2018, he met A Hao (a pseudonym) in the QQ group with black ash production. This person is very active in the group and often sells a large number of WeChat accounts. Gong Xiaoyu took the initiative to contact A Hao, and obtained three kinds of software: AW, IG and JingTianlong.
The police quickly identified A Hao’s real identity. Ceng Hao (pseudonym) was born in Hengyang City, Hunan Province in 1987. On December 4th, 2021, Ceng Hao was arrested by investigators in Changsha, Hunan Province. At this time, he was no longer engaged in the criminal activities of illegally registering WeChat accounts.
According to the investigation, the criminal gangs led by A Hao used the same method to produce and register more than two million micro-signals, making illegal profits of more than 10 million yuan. According to A Hao, Jing Tianlong, the software he sold as an agent, was recommended to him by a netizen named Wuji. A Hao didn’t know the real name of Wuji, but they met in Guangzhou.
In A Hao’s eyes, "Wuji" has superb technology and is the godfather of this circle. Many people with high academic qualifications have been bought by him. Under the investigation along the line, the police locked in a man named A Ran (Li Yiran). Li Yiran (pseudonym)
Born in luoding city, Guangdong Province in 1987. On January 17, 2022, in a high-end residential area in Nansha District, Guangzhou, investigators arrested the suspect Li Yiran.
After investigation, in 2019, Li Yiran, who only had a junior high school education, realized that there were business opportunities for changing the software, set up a Yingran Technology Co., Ltd., and recruited a number of highly educated computer software developers.
One of the best is Fan Wu (a pseudonym). Fan Wu was born in 1980 and graduated from South China University of Technology with a Ph.D. degree. Under the leadership of Fan Wu, they developed a software called IG, which was provided to WeChat registrants. But soon, this software became popular in the black and gray industrial chain of batch registration of WeChat. At the end of 2019, Li Yiran’s intention to register and develop software for WeChat in batches became more and more obvious, and Fan Wu and Li Yiran parted ways.
Li Yiran took two technicians-Chen Lin (a pseudonym) and Ma Haitao (a pseudonym) to Thailand to continue to develop the software for changing the aircraft, and then developed JingTianlong software, the success rate of which was much higher than that of IG. In order to escape the blow, they switched to virtual currency bitcoin for transaction settlement.

As gangs of electric fraud and online gambling will also pay attention to the sources of these WeChat accounts, a fraud-related company in Cambodia quickly targeted Li Yiran and others. In July 2020, Li Yiran was invited to Cambodia. But here, they are not only forced to continue to upgrade their software, but also see with their own eyes that some people use WeChat to cheat their domestic compatriots.
At the beginning of 2021, Li Yiran cheated his passport back from a fraud gang, and fled back to Guangzhou with Ma Haitao and Li Lin separately, leaving the black and gray industry circle.
The day after Li Yiran was arrested, Zhoucun police arrested Fan Wu in Dongguan City, Guangdong Province. After being arrested, Fan Wu felt a little wronged. He thought that he should not bear legal responsibility for the social harm caused by JingTianlong’s software.
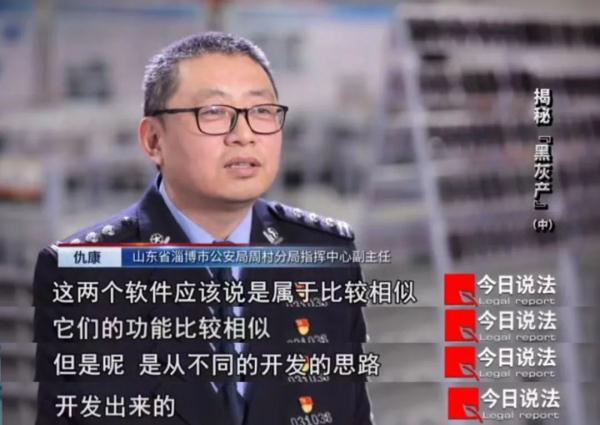
While arresting the JingTianlong software development gang, Zhoucun police also arrested two suspects who developed AW software.
A steady stream of empty resources
After arresting two criminal gangs that developed software to change mobile phones, the police shifted the focus of investigation to the source of mobile phone numbers. Gong Xiaoyu confessed that the mobile phone numbers he used to register WeChat were all empty numbers, which were provided by two netizens he met in the black and gray production circle.
Among them, A Peng (pseudonym) was born in 1989 in Shaowu City, Fujian Province; A Chao (pseudonym) was born in fengcheng city, Jiangxi Province in 1987. The two have lived in Xiamen, Fujian Province for a long time and jointly carried out illegal and criminal activities such as illegally registering WeChat accounts. At the beginning of 2018, A Peng met a dealer named Angkor in the black ash production circle and obtained sufficient empty number resources. A Peng also provided his mobile phone number to gangs all over the country.
Although these mobile phone numbers are empty, they can send and receive SMS verification codes. The staff of the operator told the police that whether it is an empty number or a real name number, the short message gateway server of the provincial operator sends and receives short messages. The police speculated that there might be a mole in the provincial operators.
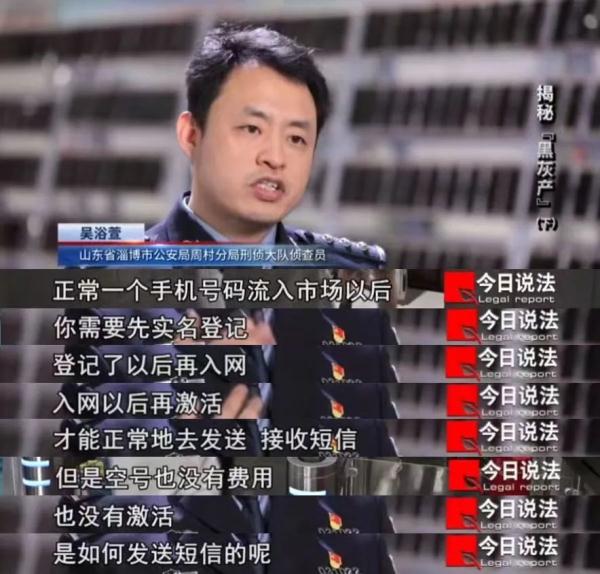
The police also made a judgment on Angkor and determined its true identity. Wu Dapeng (pseudonym) was born in Wuhu City, Anhui Province in 1980. Through the investigation of his social relations, the police found that Wu Dapeng had close contacts with two heads of a technology company in Hefei, Anhui Province.
One of the person in charge is Liu Yue (a pseudonym). After investigation, he cooperated with Tian Lin (a pseudonym), a ghost in Henan Telecom, to provide Wu Dapeng with the number. Tian Lin cheated the internal audit of the operator by signing a false number pool business contract, set up a server in the operator’s computer room, illegally invaded the operator’s SMS gateway system, provided the interface to the downstream WeChat registrant, and then extracted the empty number resources through the operator’s number pool, using a large number of empty numbers to receive and send SMS verification codes.
Through the false number pool business, Liu Yue got a large number of mobile phone numbers from a provincial operator in Henan. After several years, both Liu Yue and Tian Lin have gained great benefits.

Qi Tian (pseudonym), another person in charge of the technology company, also connected operators in Jiangsu, Jilin and Fujian for Wu Dapeng.
Since May 2022. Zhoucun police have successively arrested the ghosts in the operators. The police recovered more than 80 million pieces of mobile phone number data from their computers, which means that 80 million mobile phone numbers were used to register WeChat.
These people who convey benefits to criminals are mostly middle managers with power and important positions in the provincial companies of operators. Although they knew their behavior was illegal, they never thought about breaking the law.
With the arrival of the last telecom operator’s mole, an extraordinarily serious black ash production case investigated by Zibo police in Shandong Province for nearly two years came to an end. The 9.16 mega-black-gray-production series supervised by the Ministry of Public Security destroyed 10 criminal gangs, arrested 135 suspects, seized more than 200 million yuan of assets involved and committed more than 5,000 mobile phones, completely cutting off a black-gray-production interest chain that provided services such as WeChat accounts to overseas criminal gangs.
Law popularization time
pufashijian

Q1:
In this case, there is a new term called black ash production. Please explain to us what is black ash production?
A1:
The so-called black and gray production is the use of information networks to commit crimes, then it includes black industrial chain (black production) and gray industrial chain (gray production). The so-called "black property" means that the law has clearly stipulated that it is illegal and criminal in nature. For example, stealing accounts and phishing websites, while gray products are not explicitly prohibited by law and are in a vague zone between legal and illegal, such as malicious registration and false authentication. Then gray production often provides assistance or creates conditions for all kinds of cyber crimes, so it is also harmful to society. Nowadays, all kinds of cyber crimes have been chained and industrialized, and it is far from enough to just crack down on them. Then the concept of network black ash production reflects a change from focusing on cracking down on cases to source management and comprehensive management.
Q2:
In this case, Gong Xiaoyu illegally registered WeChat account and sold WeChat account. What kind of legal responsibility should he bear for this behavior?
A2:
Gong Xiaoyu’s behavior meets the constitutive requirements of the two charges. The first charge is that if the micro-signal he sells is actually used for telecommunication network fraud, he will be suspected of helping information network criminal activities, that is, knowing that others commit cyber crimes and providing information technology support, which is a serious act. The other is that he illegally obtained the registration information of WeChat by changing the machine software, bypassing Tencent’s security review, etc. This means is in line with the crime of illegally obtaining the data of the computer information system, that is, in violation of state regulations, using technical means to illegally obtain the data stored and transmitted in the computer information system except for state affairs and national defense construction cutting-edge technology and information systems, and the circumstances are serious.
Then, in the case that one act violates two crimes at the same time, the Criminal Law stipulates that one felony should be punished, so the maximum penalty for the crime of helping information network criminal activities is three years’ imprisonment, while the maximum statutory penalty for the crime of illegally obtaining computer information system data is seven years’ imprisonment. Therefore, Gong Xiaoyu’s behavior should be punished as the crime of illegally obtaining computer information system data.
Q3:
Gong Xiaoyu learned his criminal methods from a Hunan netizen A Hao. Do you think A Hao should bear legal responsibility?
A3:
A Hao has two behaviors. One is that he provides Gong Xiaoyu with the software to change the machine and earns the difference. The other is that he himself engages in some illegal registration and selling of micro-signals. For the former behavior, he and Gong Xiaoyu constitute a trading relationship between buyers and sellers. He (A Hao) is not responsible for these behaviors that Gong Xiaoyu illegally registers and sells micro-signals after purchasing the software to change the machine. However, he must bear the responsibility for his own illegal registration and sale of micro-signals, so the specific charge, like Gong Xiaoyu, is suspected of illegally obtaining computer information system data.
Q4:
In this case, Li Yiran only has a junior high school education. He should be a layman in developing the software for changing the machine. Compared with those highly educated R&D personnel, who will bear more legal responsibilities?
A4:
When there are such people who commit crimes together and determine whether the criminal responsibility of the perpetrators is light or heavy, it is determined according to their position and role in the crime. Then if the perpetrator plays a major role in the crime or is the organizer or leader of a criminal gang, he needs to take responsibility for all the crimes he organizes and participates in. Then, according to the principle that the punishment is consistent with the crime, the punishment of the principal is usually heavier than that of the non-principal So in this case, Li Yiran registered a technology company and enlisted a group of so-called technical talents. It was he who proposed to use virtual currency to settle accounts, and he also had the most share of the spoils. All these show that Li Yiran played a major role in the crime, so he should be punished according to the principle of punishment for the principal offender.
Q5:
When Li Yiran was engaged in illegal and criminal activities, he later settled with virtual currency bitcoin. What are the characteristics of virtual currency, such as bitcoin, and what are the management regulations for virtual currency in China’s laws?
A5:
The so-called virtual currency is actually a special Internet commodity. It does not have the property of currency and cannot be circulated in the market. So at present, individuals are not prohibited from holding virtual currency in our country. However, if virtual currency is used to carry out some illegal and criminal activities, it is of course necessary to bear corresponding legal responsibilities.
Q6:
What are the risks if citizens hold virtual currency?
A6:
If citizens hold or invest in virtual currency, the risk is great. On the one hand, the transaction process and pricing mechanism of virtual currency are opaque, so the price fluctuates greatly and it is easy to suffer economic losses; On the other hand, due to the lack of supervision, virtual currency is often used by cyber crimes to implement some behaviors, such as telecommunication network fraud, online gambling, illegal fund-raising, etc., so if you invest in virtual currency, it may involve some online illegal and criminal activities.
Q7:
There is a mole in this case, so when the mole of the telecom operator provided this convenience to the suspect, they said that they didn’t expect such behavior to be suspected of committing a crime. What kind of legal responsibility do you think they should bear?
A7:
What responsibility do these so-called telecom operators take? In one case, they set up a server in the telecom operator’s computer room and provide the interface to WeChat registrants. If so, their behavior is suspected of providing the crime of invading and illegally controlling computer information system programs and tools, that is, providing programs or tools specially used for illegally invading and illegally controlling computer information systems. In the second case, they directly drag these numbers out of this virtual number pool of telecom operators and provide them directly to WeChat registrants. If so, their behavior will be suspected of illegally obtaining computer information system data.
Source of the case | "legal report" program "Revealing the Secret" Black Ash Production (upper, middle and lower)
Reporter | Bai Min Yulin
catalogs:115814; contentid:11708791; publishdate:2023-08-12; Author: Hou Tian; file:1691838303168-d17dd684-5175-4fb6-b5e6-5b004dd73de4; source:29; From:CCTV legal report; timestamp:2023-08-12
19:04:54;